This week, security researchers at Wiz published a report about an internal database at DeepSeek being exposed to the internet. This kind of security risk is surprisingly common and can affect any company. The only way to prevent it is through continuous monitoring. But in modern infrastructures, services can be exposed in many different ways, making detection tricky.
At Coroot, we realized that the telemetry data we already collect can help identify these risks — without requiring any extra setup. So, we built a new feature that automatically audits database exposure for our users.
Coroot is an open-source observability platform powered by eBPF. Our agent already tracks all applications running on a node and discovers all TCP listen sockets. Previously, we used this data to build Service Maps. Now, we’ve expanded its capabilities.
Since Coroot automatically detects the type of every application or container, it can distinguish between database servers and stateless apps. It supports a wide range of open-source databases, including PostgreSQL, MySQL, Redis (and its alternatives), Memcached, MongoDB, Elasticsearch, OpenSearch, ClickHouse, Prometheus, VictoriaMetrics, Kafka, RabbitMQ, and more.
However, databases accepting connections on public IPs are only part of the problem. On Kubernetes, services can be exposed through a NodePort or LoadBalancer, making them accessible from the internet. Coroot already collects data about Kubernetes Services, so we’ve covered those scenarios as well.
Of course, some databases are intentionally exposed, for example, when access is controlled via firewalls, AWS Security Groups, or built-in database security mechanisms. To avoid alert fatigue, Coroot allows users to dismiss specific risks with a single click.
The best part? No extra setup is needed. Just install or upgrade Coroot to the latest version, and this feature is available immediately. It works in both the Community and Enterprise editions.
Here’s how it looks: Coroot detected three databases exposed to the internet, showing the exact IP addresses and ports. In this example, OpenSearch and VictoriaMetrics are running outside Kubernetes with direct public IPs, while PostgreSQL is exposed via a NodePort service.
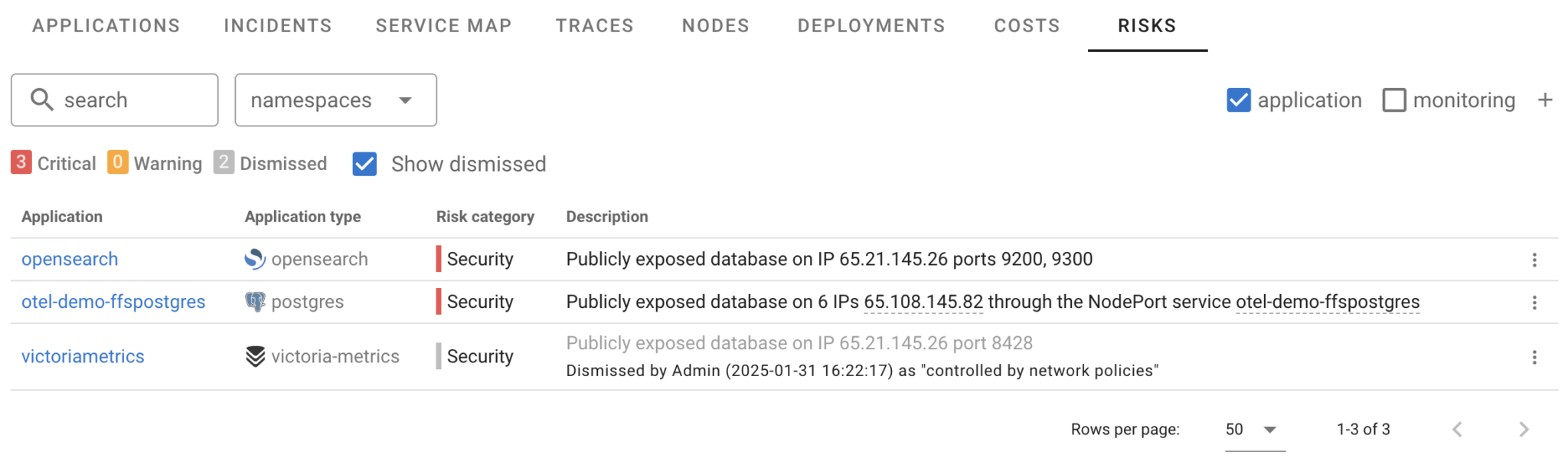
And if an alert isn’t relevant, you can dismiss it instantly:
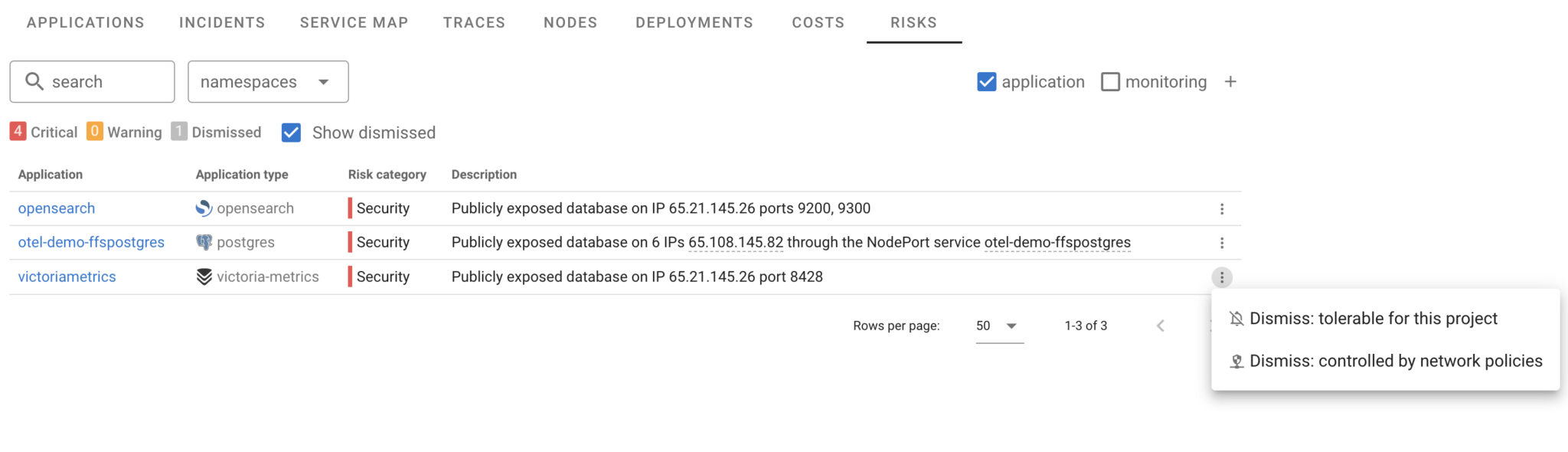
This feature is fully integrated with Coroot’s Role-Based Access Control, ensuring only authorized users can view and manage these risks.
At Coroot, we believe in delivering immediate value without requiring complex integrations or configurations, and this feature is no exception.
Give Coroot a try and make sure none of your databases are unintentionally exposed. Along the way, you’ll also gain deep visibility into your system’s performance, security risks, and even costs.
Get started with the free Coroot Community Edition or explore advanced features with a free trial of Coroot Enterprise Edition.
If you like Coroot, give us a ⭐ on GitHub️.
Any questions or feedback? Reach out to us on Slack.